 A number of digital health apps in the Google Play store send unencrypted information over the internet and use of third party services, according to a graduate thesis from University of Illinois at Urbana-Champaign student Dongjing He.
A number of digital health apps in the Google Play store send unencrypted information over the internet and use of third party services, according to a graduate thesis from University of Illinois at Urbana-Champaign student Dongjing He.
Before conducting the study, He formulated three questions. The first was what are the potential "attack surfaces" for Android digital health apps? The second, how widespread is the threat? And the last one, how serious is the threat?
To find the potential "attack surfaces", He looked for security issues identified in previous research studies conducted at the Association for Computing Machinery, University of California Berkeley, F-Secure Labs, and University of Illinois at Urbana-Champaign. Later when she analyzed the tools, He used the "Shark for Root" app to capture network traffic.
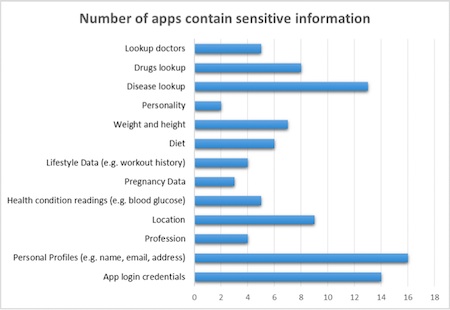
She pulled the top 80 free apps from the health and fitness category in the Google Play store and the top 80 free apps in the medical category. From there, He found that the most prevalent six areas that need protections include sending information over the internet, storing information on third party servers, collecting information via Bluetooth, adding sensitive information to system logs, storing information on the SD card as an unencrypted file, and "accessing Android app components from other apps, which are intended to be private, but set as exported".
After He identified the "attack surfaces" in the first study, she moved on to analyze how prevalent this threat is in the app store. He chose to analyze 27 apps at random from a list of the top 1,080 free apps in the health and fitness and medical categories in the Google Play store. After an analysis He pinpointed three "attack surfaces" that were common in these apps -- sending unencrypted information through the internet via unsecure protocols, storing information on third party servers, and logging information on the app.
He found that 23 out of 27 apps had permission to use the internet and 19 of those 23 used the internet to display ads while eight used the internet to send information. Three apps sent unencrypted information over the internet.
When apps store user data in their logs, that information can be accessible by malicious apps. Nine out of 27 apps stored data in the app's logs. Among the 9 apps, two stored GPS coordinates, three stored Facebook friend information, one stored the user's directions to a dentist office, and another one stored sensitive data including the user's name, location and profession.


















